Kerberos double hop
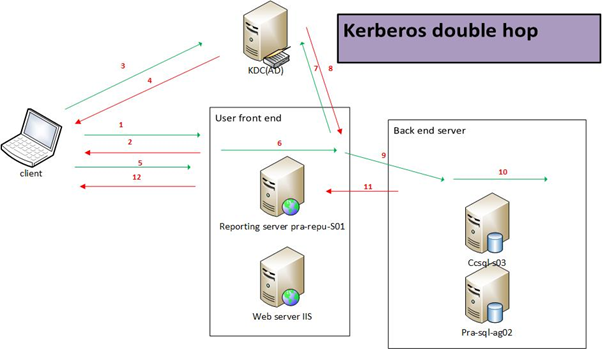
1. users access http://pra-repu using anonymous credentials.
2. The reporting Server returns error 401.2 and returns an Authenticate header.
3. users request a ticket for the SPN created by the local network: http://pra-repu
4. The KDC returns the ticket if the SPN is found. This is encrypted using the registered account master key for the SPN (fednot\gen_rep).
5. Users authenticates with the ticket for the web application.
6. The Web App account decrypts the ticket and validates it.
7. Web App account requests ticket for the SPN created by the SQL Client: MSSqlSvc/ccsql-s03.fednot.be:1433.
8. The KDC returns the ticket if the SPN is found. This is encrypted using the registered account master key for the SPN (fednot \gen_sql).
9. The web application service authenticates with the SQL database using the Web App account ticket and impersonates the user using delegation rights.
10. The SQL service account decrypts the ticket and validates it.
11. The SQL Server returns the request data to the WSS Server.
12. The WSS Server returns the webpage.